Linux Navigation and Commands
Linux is an operating system used in cybersecurity. Learning Linux commands and navigation through the operating system is vital for a cybersecurity professional. Useful websites for Linux commands are
- SS64 most commonly used syntax
- explainshell helps understand and use complex command-line tools and utilities. It explains clear and concisely
- man documentation for many used Linux commands
This is what the terminal looks like.

Let’s get started with two of the first commands which I have broken down in the table below:
| Command | Description |
| echo | Output any text that we provide |
| whoami | Find out what user we’re currently logged in as! |

Interacting with the Filesystem– what’s the point of logging in if we can’t go anywhere?
| Command | Full Name |
| ls | listing |
| cd | change directory |
| cat | concatenate |
| pwd | print working directory |
>>Listing Files in Our Current Directory (ls)– Before we can do anything such as finding out the contents of any files or folders, we need to know what exists in the first place. This can be done using the “ls” command (short for listing)
>>Changing Our Current Directory (cd)– Now that we know what folders exist, we need to use the “cd” command (short for change directory) to change to that directory. Say if I wanted to open the “Pictures” directory – I’d do “cd Pictures“. Where again, we want to find out the contents of this “Pictures” directory and to do so, we’d use “ls” again
>>Outputting the Contents of a File (cat)– Whilst knowing about the existence of files is great — it’s not all that useful unless we’re able to view the contents of them.
We will come on to discuss some of the tools available to us that allows us to transfer files from one machine to another in a later room. But for now, we’re going to talk about simply seeing the contents of text files using a command called “cat”.
“Cat” is short for concatenating & is a fantastic way us to output the contents of files (not just text files!).
In the screenshot below, you can see how I have combined the use of “ls” to list the files within a directory called “Documents”
>>Finding out the full Path to our Current Working Directory (pwd)
Searching for Files– No need to consistently use cd and ls to find out what is where. Instead, we can use commands such as find to automate things like this for us!
>>Using Find–
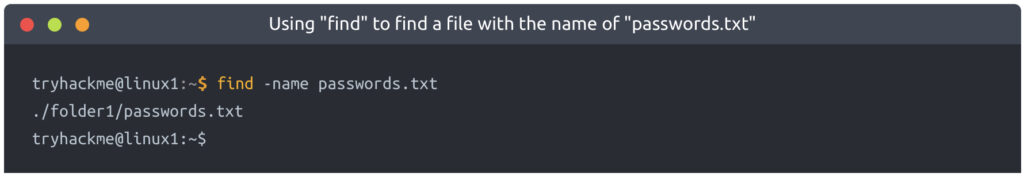
Let’s start simple and assume that we already know the name of the file we’re looking for — but can’t remember where it is exactly! In this case, we’re looking for “passwords.txt”
If we remember the filename, we can simply use find -name passwords.txt where the command will look through every folder in our current directory for that specific file like so:
Say that we don’t know the name of the file, or want to search for every file that has an extension such as “.txt”. Find let’s us do that too!
We can simply use what’s known as a wildcard (*) to search for anything that has .txt at the end. In our case, we want to find every .txt file that’s in our current directory. We will construct a command such as find -name *.txt . Where “Find” has been able to find every .txt file and has then given us the location of each one:
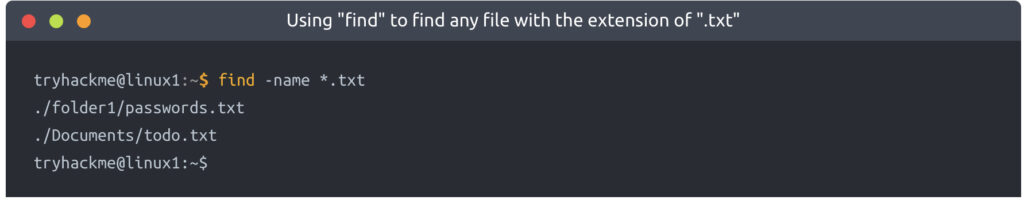
Find has managed to find:
- “passwords.txt” located within “folder1”
- “todo.txt” located within “Documents”
>>Using Grep–

Intro to shell operators–
| Symbol / Operator | Description |
| & | This operator allows you to run commands in the background of your terminal. |
| && | This operator allows you to combine multiple commands together in one line of your terminal. |
| > | This operator is a redirector – meaning that we can take the output from a command (such as using cat to output a file) and direct it elsewhere. |
| >> | This operator does the same function of the > operator but appends the output rather than replacing (meaning nothing is overwritten). |
Secure Shell or SSH for short and is the common means of connecting to and interacting with the command line of a remote Linux machine.
What is SSH & how Does it Work?
Secure Shell or SSH simply is a protocol between devices in an encrypted form. Using cryptography, any input we send in a human-readable format is encrypted for travelling over a network — where it is then unencrypted once it reaches the remote machine, such as in the diagram below.

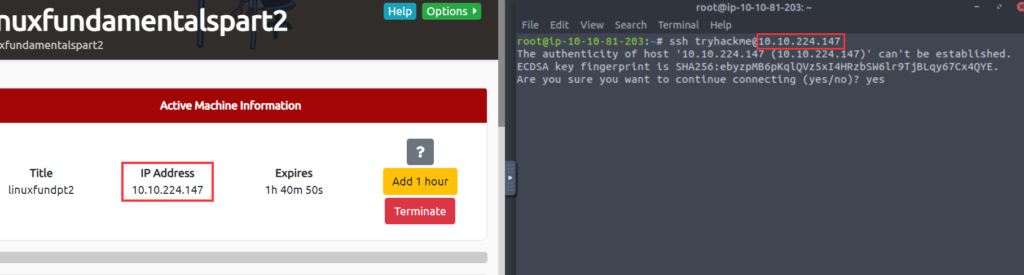
Using SSH to Login to Your Linux Machine
For example: ssh tryhackme@MACHINE_IP . Replacing the IP address with the IP address for your Linux target machine. Once executed, we will then be asked to trust the host and then provide a password for the “tryhackme” account, which is also “tryhackme“.
Flags and Switches– A majority of commands allow for arguments to be provided. These arguments are identified by a hyphen and a certain keyword known as flags or switches.
Using our ls example, ls informs us that there is only one folder named “folder1” as highlighted in the screenshot below. Note that the contents in the screenshots below are only examples.
Using ls to view the contents of a directory
tryhackme@linux2:~$ ls
folder1
tryhackme@linux2:~$However, after using the -a argument (short for --all), we now suddenly have an output with a few more files and folders such as “.hiddenfolder”. Files and folders with “.” are hidden files.
Using ls to view hidden folders
tryhackme@linux2:~$ ls -a
.hiddenfolder folder1
tryhackme@linux2:~$Commands that accept these will also have a--help option. This option will list the possible options that the command accepts, provide a brief description and example of how to use it.
tryhackme@linux2:~$ ls –help
The manual pages are a great source of information for both system commands and applications available on both a Linux machine, which is accessible on the machine itself and online.
tryhackme@linux2:~$ man ls
Filesystem Interaction–
| Command | Full Name | Purpose |
| touch | touch | Create file |
| mkdir | make directory | Create a folder |
| cp | copy | Copy a file or folder |
| mv | move | Move a file or folder |
| rm | remove | Remove a file or folder |
| file | file | Determine the type of a file |
Using touch to create a new file
tryhackme@linux2:~$ touch note
tryhackme@linux2:~$ ls
folder1 noteCreating a new directory with mkdir
tryhackme@linux2:~$ mkdir mydirectory
tryhackme@linux2:~$ ls
folder1 mydirectory noteUsing rm to remove a file
tryhackme@linux2:~$ rm note
tryhackme@linux2:~$ ls
folder1 mydirectoryUsing rm recursively to remove a directory
tryhackme@linux2:~$ rm -R mydirectory
tryhackme@linux2:~$ ls
folder1Using cp to copy a file
tryhackme@linux2:~$ cp note note2
tryhackme@linux2:~$ ls
folder1 note note2Using mv to move a file
tryhackme@linux2:~$ mv note2 note3
tryhackme@linux2:~$ ls
folder1 note note3Using file to determine the contents of a file
tryhackme@linux2:~$ file note
note: ASCII textPermission–
Using ls -lh to list the permissions of all files in the directory
tryhackme@linux2:~$ ls -lh
-rw-r--r-- 1 cmnatic cmnatic 0 Feb 19 10:37 file1
-rw-r--r-- 8 cmnatic cmnatic 0 Feb 19 10:37 file2Using su to switch to user2
tryhackme@linux2:~$ su user2
Password:
user2@linux2:/home/tryhackme$Using su to switch to user2 interactively
tryhackme@linux2:~$ su user2
Password:
user2@linux2:/home/tryhackme$For example, when using su to switch to “user2”, our new session drops us into our previous user’s home directory.
Using su to switch to user2 interactively
tryhackme@linux2:~$ su -l user2
Password:
user2@linux2:~$ pwd
user2@:/home/user2$Where now, after using -l, our new session has dropped us into the home directory of “user” automatically.
Networking Foundations
Understand how the internet works. Basics of networking. How data travels in packets and frames. Learn TCP/IP (This protocol governs the communication between devices and allows the world to be connected)